Note: This post now archived and as such no longer works

This is possible because Lemmy doesn’t proxy external images but instead loads them directly. While not all that bad, this could be used for Spy pixels by nefarious posters and commenters.
Note, that the only thing that I willingly log is the “hit count” visible in the image, and I have no intention to misuse the data.
The best part is it also works on DMs, so it’s trivial to get any persons IP address. Want an admins IP address? Just DM them a message with an embedded spy pixel.
I emailed the lemmy developers about this a few weeks ago since IMHO it’s a pretty big security issue, no reply.
I think you’re overestimating the value of someone’s IP address. Not much one can do with it unless someone really tries to expose themselves.
-
If you are planning on hijacking one of their online accounts, then obtaining all possible intel about someone helps to make phishing their other service providers easier. Knowing someone’s IP address means you instantly know what city they are in and who their service provider is.
-
If you are trying to reveal someone’s true identity and you have already learned of their IP address through some other means, then this would allow you to reveal their identity on lemmy. Example: an employer already knows the home ip addresses of their employees who work remotely and vpn into the company office. They see someone on lemmy sharing insider info about the company they would rather not have shared and suspect the lemmy user is a disgruntled employee and send them a dm with tracking pixel to verify whether that lemmy user’s ip address matches the addresses of any of their employees.
-
Consider the case of someone thinking they are anonymous and boasting about some activities that might be legally questionable, then consider some law enforcement agency using tracking pixel to get user’s ip address. If the lemmy server is outside of jurisdiction they might not be able to subponea the lemmy instance admins for that user’s ip address, but now they don’t have to. With the IP address they can just subponea the isp to get the user’s identity. This could be over criminal activity…or maybe just something like admitting being gay in a country that sentences to death for that.
These are just three examples…there are countless other examples just as bad.
TL/DR: it is a significant security breach to allow 3rd parties the ability to use the platform to expose user’s ip addresses, and even worse when it can be targeted at specific users (such as the DM scenerio that is also affected).
-
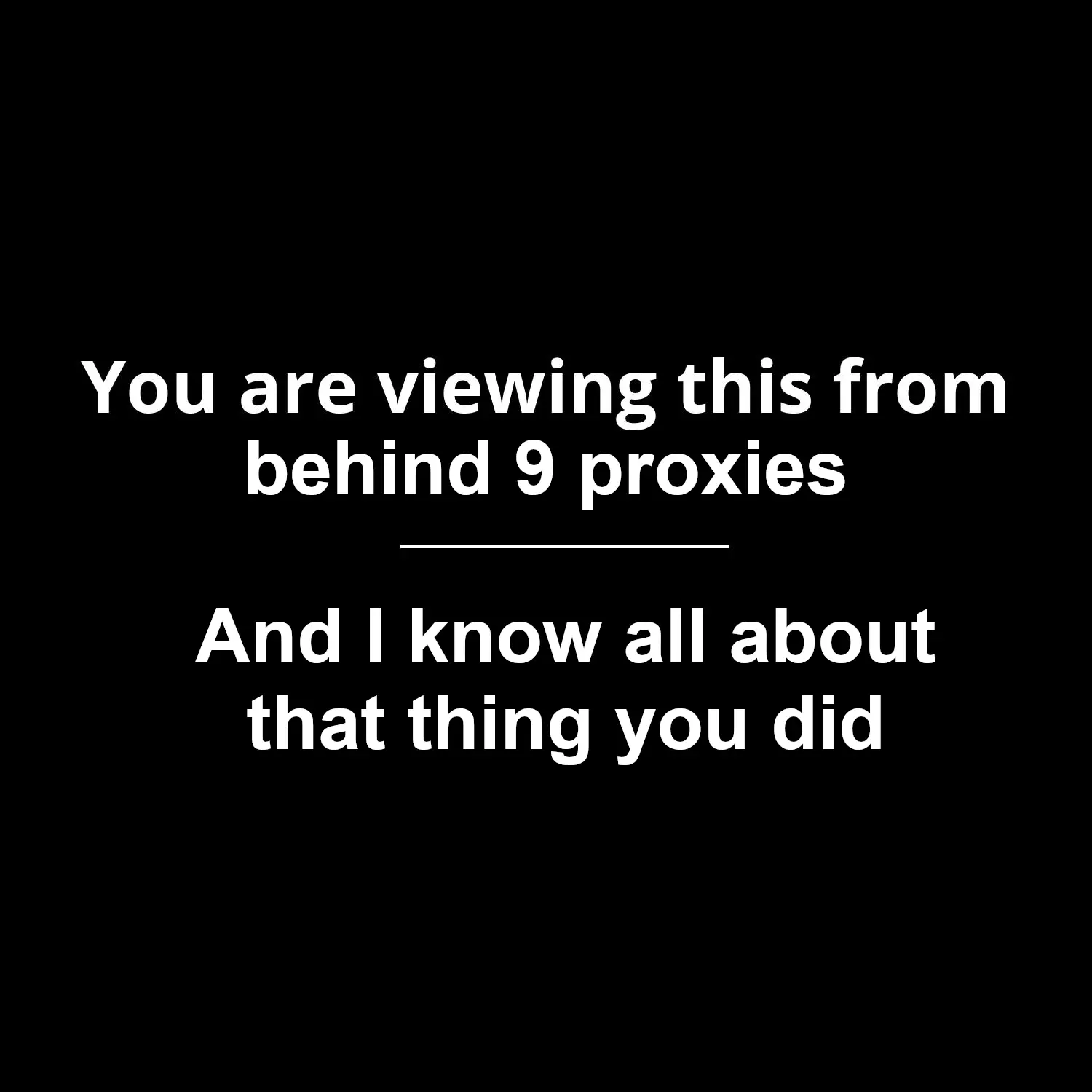
Joke’s on you, I’m in front of 9 proxies. 🤡
1: DM all admins a spy pixel.
2: Coordinate a mass effort to spam rule-breaking posts and comments at some day.
3: Distributed denial of service attack on all admin IPs on that day.
…
Profit?
I’m on kbin, so tell me: do the images open on their own on Lemmy? If not, then it works like any link one might send, image or not image. The server always can see the IP address, as it was never meant to be secret. This also assumes the admins always use a single network with a single static IP address.
Embeds are fetched and displayed without user interaction.
This also assumes the admins always use a single network with a single static IP address.
Not really. Send a DM to every single admin of an instance and wait until you get enough collected IP addresses. Pay someone running a botnet to flood those addresses for an hour or two.
Even with a dynamic IP address, you’re still stuck with it for a while. If you’re lucky, power cycling will get a new one immediately. If you’re not you get to enjoy waiting for a day or sitting on hold with your ISP’s support number, running through their scripted support process until you finally get to someone capable of helping.
Didn’t knew you can DM on lemmy. Maybe the Jerboa devs have not implemented it yet.
Not really.
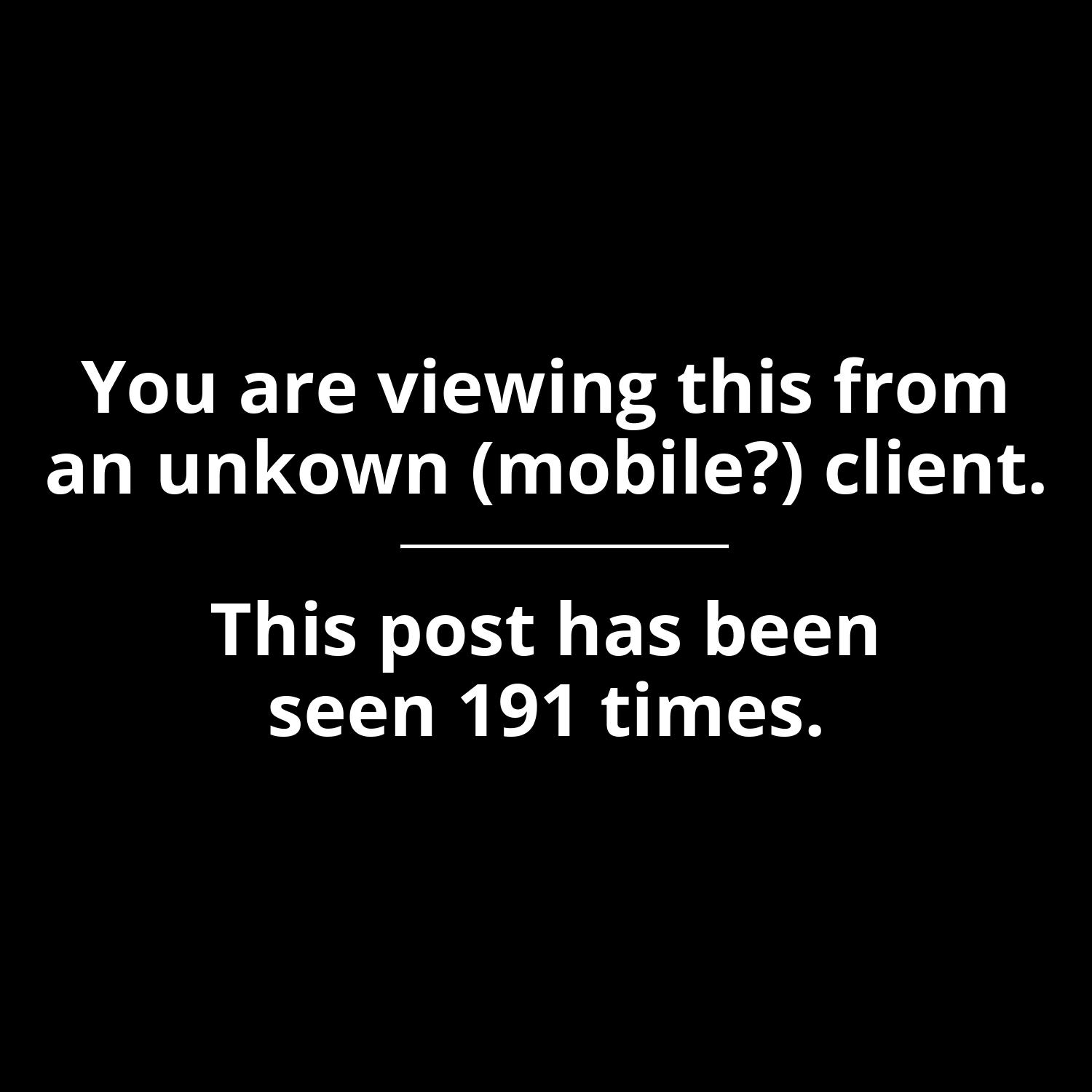
Same, I’m using an app.
Jerdoa
“an unknown (mobile?) client”
Well, nice try anyway.
sPoOky
Same, woo for my security I guess!

uBlock Origin? NoScript? Internet Explorer?
Liftoff, and the device has Blokada5 running but it didn’t block that.
It got my OS right, but browser wrong. Tested both Librewolf and Vivaldi, which it sees as Firefox and Chrome.
This is because librewolf reports itself as firefox for privacy, and vivaldi does the same thing with chrome. Their is no vivaldi string in their user agent.
That makes sense. Vivaldi uses a chrome user agent most of the time, unless you use a Microsoft service, in which case it uses a Microsoft Edge user agent.
The post know where I am because it knows where I am not.
You are viewing this from a
(rand() % 2 == 0) ? "android" : "apple"phone.“You are viewing this from bile Safari”
It did not get my setup right. I guess that newsboat+PostmarketOS+Pinephone is exotic enough.
Hello fellow pinephone enjoyer. I haven’t used mine in a while. Has the battery life situation improved much?
Not really. I use it without SIM card, with the extra battery housed in the keyboard I have to plug it every 2 days.
One day…
Right client, wrong operating system. It knows I’m using Leomard, but it thinks I’m on iOS. I suspect it doesn’t handle architecture detection well on Apple Silicon machines.
“You are viewing this from ome Mobile web View on Andr”… Uhhhh… Ok?
Very interesting, I think I’ll probably be using Tor for my Lemmy usage from now on, or at least a VPN since this does have the potential to be used maliciously in personal DDoS attacks.
Your IP isn’t a secret. There plenty of ways to get it. And this one doesn’t even link it to your identity
It’s not about identification it’s about being disconnected in a DoS by someone with faster internet (until I can get a new one, dynamic IP rotates).
DoS is expensive. Who the hell would spend money just to get you disconnected? Nobody cares about your connection
Annoyingly, lemmy.world blocks tor. They should host a tor onion service
Are you sure about that because I can open and view lemmy.world just fine in Tor, I think what they mean is federation between hidden services i.e. lemmyinstanceoniondomain.onion is blocked or just not implemented.
I can if I use a browser and solve the cloud flare capt ha, but not if I use sync behind tor
I haven’t gotten Cloudflare captchas on lemmy.world yet, Haven’t tried using an app with Tor, as a general rule it’s best to use Tor through the browser since it has features to reduce fingerprinting and MITMs
Removed by mod
Probably the image is cached.
Removed by mod
Whatever Software you’re using to view this caches the image
What is the functioning process of this?
A simple GET request.
deleted by creator
Your assumption that doxxing is somehow the only valid privacy/security concern is misguided.
deleted by creator
This is Lemmy, you are willing to let people know you use windows??
deleted by creator
Now you’re just trying to pick a fight.